- Netextender Download
- Sonicwall Netextender For Mac Remote Desktop
- Sonicwall Netextender For Mac
- Sonicwall Netextender For Mac Download
- Sonicwall Netextender For Mac Remote Desktop
SonicWALL's SSL VPN NetExtender feature is a transparent software application for Windows, Mac, and Linux users that enables remote users to securely connect to the remote network. With NetExtender. Net Extender is deprecated for MAC OS 10.9 (Mavericks) and 10.10 (Yosemite). Support is limited to critical bugs and security vulnerabilities only. Please use SonicWall Mobile Connect instead. SonicWall's SSL VPN NetExtender allows you to provide easy and secure access to Windows and Linux users. This transparent software enables remote users to securely connect and run any application on the company network. Users can upload and download files, mount network drives, and access resources as if they were on the local network.
SSL_VPN
SSL VPN
This section provides information on how to configure the SSL VPN features on the Dell SonicWALL network security appliance. SonicWALL's SSL VPN features provide secure remote access to the network using the NetExtender client.
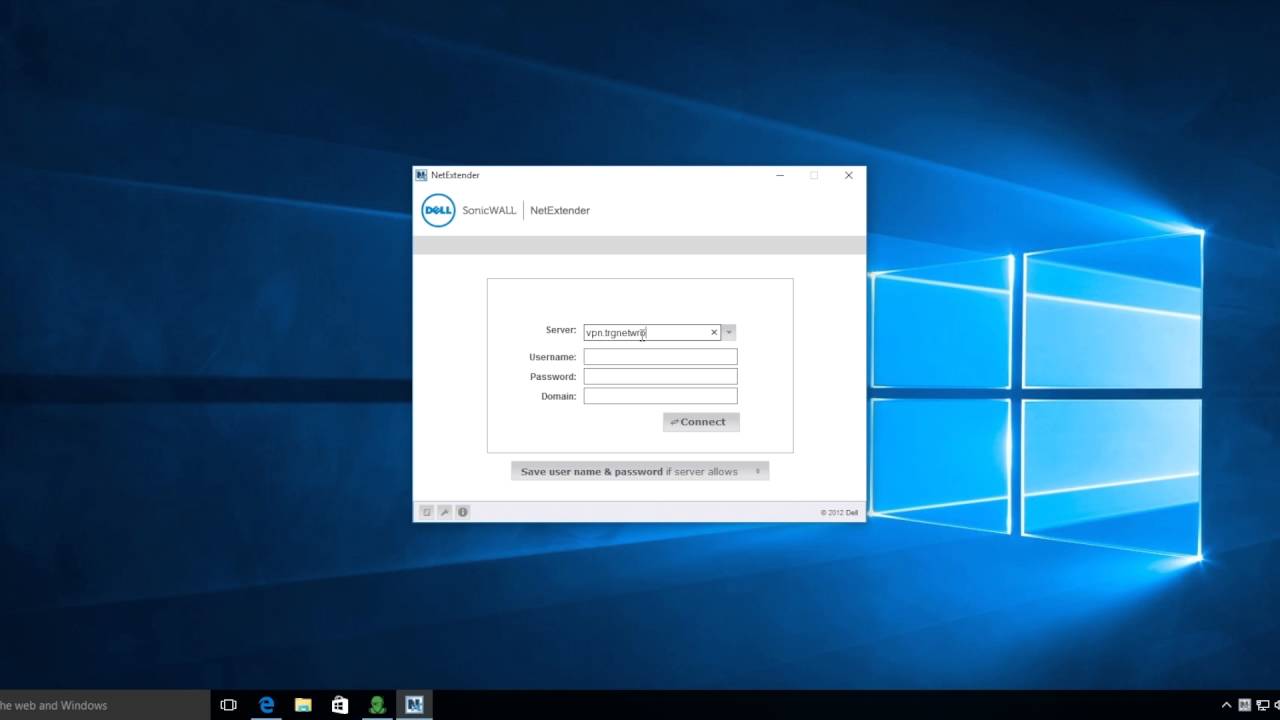
NetExtender is an SSL VPN client for Windows, Mac, or Linux users that is downloaded transparently and that allows you to run any application securely on the company's network. It uses Point-to-Point Protocol (PPP). NetExtender allows remote clients seamless access to resources on your local network. Users can access NetExtender two ways:
• Logging in to the Virtual Office web portal provided by the Dell SonicWALL network security appliance and clicking on the NetExtender button.
• Launching the standalone NetExtender client.
The NetExtender standalone client is installed the first time you launch NetExtender. Thereafter, it can be accessed directly from the Start menu on Windows systems, from the Application folder or dock on MacOS systems, or by the path name or from the shortcut bar on Linux systems.
Topics:
• SSL VPN NetExtender Overview
• Configuring Users for SSL VPN Access
Related Topics:
• SSL VPN > Status
• SSL VPN > Server Settings
• SSL VPN > Portal Settings
• SSL VPN > Client Settings
• SSL VPN > Client Routes
• SSL VPN > Virtual Office
• Accessing the SSL VPN Portal
• Using NetExtender
• Configuring SSL VPN Bookmarks
• Using SSL VPN Bookmarks
SSL VPN NetExtender Overview
This section provides an introduction to the SonicOS SSL VPN NetExtender feature.
Topics:
• What is SSL VPN NetExtender?
• Benefits
• NetExtender Concepts
What is SSL VPN NetExtender?
SonicWALL's SSL VPN NetExtender feature is a transparent software application for Windows, Mac, and Linux users that enables remote users to securely connect to the remote network. With NetExtender, remote users can securely run any application on the remote network. Users can upload and download files, mount network drives, and access resources as if they were on the local network. The NetExtender connection uses a Point-to-Point Protocol (PPP) connection.
Benefits
NetExtender provides remote users with full access to your protected internal network. The experience is virtually identical to that of using a traditional IPSec VPN client, but NetExtender does not require any manual client installation. Instead, the NetExtender Windows client is automatically installed on a remote user's PC by an ActiveX control when using the Internet Explorer browser, or with the XPCOM plugin when using Firefox. On MacOS systems, supported browsers use Java controls to automatically install NetExtender from the Virtual Office portal. Linux systems can also install and use the NetExtender client.
After installation, NetExtender automatically launches and connects a virtual adapter for secure SSL-VPN point-to-point access to permitted hosts and subnets on the internal network.
NetExtender Concepts
The following sections describe advanced NetExtender concepts:
• Stand-Alone Client
• Client Routes
• Tunnel All Mode
• Connection Scripts
• Proxy Configuration
Stand-Alone Client
NetExtender is a browser-installed lightweight application that provides comprehensive remote access without requiring users to manually download and install the application. The first time a user launches NetExtender, the NetExtender stand-alone client is automatically installed on the user's PC or Mac. The installer creates a profile based on the user's login information. The installer window then closes and automatically launches NetExtender. If the user has a legacy version of NetExtender installed, the installer will first uninstall the old NetExtender and install the new version.
Once the NetExtender stand-alone client has been installed, Windows users can launch NetExtender from their PC's Start > Programs menu and configure NetExtender to launch when Windows boots. Mac users can launch NetExtender from their system Applications folder, or drag the icon to the dock for quick access. On Linux systems, the installer creates a desktop shortcut in /usr/share/NetExtender. This can be dragged to the shortcut bar in environments like Gnome and KDE.
Client Routes
NetExtender client routes are used to allow and deny access for SSL VPN users to various network resources. Address objects are used to easily and dynamically configure access to network resources.
Tunnel All Mode
Tunnel All mode routes all traffic to and from the remote user over the SSL VPN NetExtender tunnel—including traffic destined for the remote user's local network. This is accomplished by adding the following routes to the remote client's route table:
|
NetExtender also adds routes for the local networks of all connected Network Connections. These routes are configured with higher metrics than any existing routes to force traffic destined for the local network over the SSL VPN tunnel instead. For example, if a remote user is has the IP address 10.0.67.64 on the 10.0.*.* network, the route 10.0.0.0/255.255.0.0 is added to route traffic through the SSL VPN tunnel.
Tunnel All mode is configured on the SSL VPN > Client Routes page. See SSL VPN > Client Routes.
Connection Scripts
SonicWALL SSL VPN provides users with the ability to run batch file scripts when NetExtender connects and disconnects. The scripts can be used to map or disconnect network drives and printers, launch applications, or open files or Web sites. NetExtender Connection Scripts can support any valid batch file commands.
Proxy Configuration
SonicWALL SSL VPN supports NetExtender sessions using proxy configurations. Currently, only HTTPS proxy is supported. When launching NetExtender from the Web portal, if your browser is already configured for proxy access, NetExtender automatically inherits the proxy settings. The proxy settings can also be manually configured in the NetExtender client preferences. NetExtender can automatically detect proxy settings for proxy servers that support the Web Proxy Auto Discovery (WPAD) Protocol.
NetExtender provides three options for configuring proxy settings:
• Automatically detect settings - To use this setting, the proxy server must support Web Proxy Auto Discovery Protocol (WPAD)), which can push the proxy settings script to the client automatically.
• Use automatic configuration script - If you know the location of the proxy settings script, you can select this option and provide the URL of the script.
• Use proxy server - You can use this option to specify the IP address and port of the proxy server. Optionally, you can enter an IP address or domain in the BypassProxy field to allow direct connections to those addresses and bypass the proxy server. If required, you can enter a user name and password for the proxy server. If the proxy server requires a username and password, but you do not specify them, a NetExtender pop-up window will prompt you to enter them when you first connect.
When NetExtender connects using proxy settings, it establishes an HTTPS connection to the proxy server instead of connecting to the firewall server directly. The proxy server then forwards traffic to the SSL VPN server. All traffic is encrypted by SSL with the certificate negotiated by NetExtender, of which the proxy server has no knowledge. The connecting process is identical for proxy and non-proxy users.
Configuring Users for SSL VPN Access
For users to be able to access SSL VPN services, they must be assigned to the SSLVPN Services group. Users who attempt to login through the Virtual Office who do not belong to the SSLVPN Services group will be denied access. The following sections describe how to configure user accounts for SSL VPN access:
• Configuring SSL VPN Access for Local Users
• Configuring SSL VPN Access for RADIUS Users
• Configuring SSL VPN Access for LDAP Users
Configuring SSL VPN Access for Local Users
To configure users in the local user database for SSL VPN access, you must add the users to the SSLVPN Services user group. To do so, perform the following steps:
1. Navigate to the Users > Local Users page.
2. Click on the configure icon for the user you want to edit, or click the Add User button to create a new user. The Edit User window is launched.
3. Click on the Groups tab.
4. In the User Groups column, click on SSLVPN Services and click the right arrow to move it to the Member Of column.
5. Click on the VPN Access tab. The VPN Access tab configures which network resources VPN users (either GVC, NetExtender, or Virtual Office bookmarks) can access.
Note The VPN access tab affects the ability of remote clients using GVC, NetExtender, and SSL VPN Virtual Office bookmarks to access network resources. To allow GVC, NetExtender, or Virtual Office users to access a network resource, the network address objects or groups must be added to the 'allow' list on the VPN Access tab.
6. Select one or more network address objects or groups from the Networks list and click the right arrow button (->) to move them to the Access List column. To remove the user's access to a network address objects or groups, select the network from the Access List, and click the left arrow button (<-).
7. Click OK.
Configuring SSL VPN Access for RADIUS Users
To configure RADIUS users for SSL VPN access, you must add the users to the SSLVPN Services user group. To do so, perform the following steps:
1. Navigate to the Users > Settings page.
2. In the Authentication Method for login pull-down menu, select RADIUS or RADIUS + Local Users.
3. Click the Configure button for Authentication Method for login. The RADIUS Configuration window displays.
4. Click on the RADIUS Users tab.
5. In the Default user group to which all RADIUS users belong pull-down menu, select SSLVPN Services.
Note The VPN Access tab in the Edit User window is also another granular control on access for both Virtual Office Bookmarks and for NetExtender access.
6. Click OK.
Configuring SSL VPN Access for LDAP Users
To configure LDAP users for SSL VPN access, you must add the LDAP user groups to the SSLVPN Services user group. To do so, perform the following steps:
1. Navigate to the Users > Settings page.
2. Set the Authentication method for login to either LDAP or LDAP + Local Users.
3. Click the Configure button to launch the LDAP Configuration window.
4. Click on the LDAP Users tab.
5. In the Default LDAP User Group pull-down menu, select SSLVPN Services.
Note The VPN Access tab in the Edit User window is also another granular control on access for both Virtual Office Bookmarks and for NetExtender access.
6. Click OK.
SSL VPN > Status
The SSL VPN > Status page displays a summary of active NetExtender sessions, including the name, the PPP IP address, the physical IP address, login time, length of time logged in and logout time.
The following table provides a description of the status items.
|
SSL VPN > Server Settings
The SSL VPN > Server Settings page is used to configure details of the firewall's behavior as an SSL VPN server.
The following options can be configured on the SSL VPN > Server Settings page.
• SSL VPN Status on Zones: This displays the SSL VPN Access status on each Zone. Green indicates active SSL VPN status, while red indicates inactive SSL VPN status. To enable or disable SSL-VPN access on a zone, click on the zone name to jump to the Edit Zone window.
• SSL VPN Port: Set the SSL VPN port for the appliance. The default is 4433.
• Certificate Selection: Select the certificate that will be used to authenticate SSL VPN users. To manage certificates, go to the Network > Certificates page.
• Enable Server Cipher Preference: Select this checkbox to configure a preferred cipher method. The available ciphers are RC4_MD5, 3DES_SHA1, and AES256_SHA1.
• RADIUS User Settings: This option is only available when either RADIUS or LDAP is configured to authenticate SSL VPN users. Select the Use RADIUS in checkbox to have RADIUS use MSCHAP (or MSCHAPv2) mode. Enabling MSCHAP-mode RADIUS will allow users to change expired passwords at login time.
Note In LDAP, password updates can only be done when using either Novell eDirectory or Active Directory with TLS and binding to it using an administrative account. If LDAP is not configured as such, password updates for SSL VPN users will be performed using MSCHAP-mode RADIUS, after using LDAP to authenticate the user.
SSL VPN > Portal Settings
The SSL VPN > Portal Settings page is used to configure the appearance and functionality of the SSL VPN Virtual Office web portal. The Virtual Office portal is the website that uses log in to launch NetExtender. It can be customized to match any existing company website or design style.
The following settings configure the appearance of the Virtual Office portal:
• Portal Site Title - The text displayed in the top title of the web browser.
• Portal Banner Title - The the text displayed next to the logo at the top of the page.
• Home Page Message - The HTML code that is displayed above the NetExtender icon.
• Login Message - The HTML code that is displayed when users are prompted to log in to the Virtual Office.
• Example Template - Resets the Home Page Message and Login Message fields to the default example template.
• Preview - Launch a pop-up window that displays the HTML code.
The following options customize the functionality of the Virtual Office portal:
• Launch NetExtender after login - Automatically launches NetExtender after a user logs in.
• Display Import Certificate Button - Displays an Import Certificate button on the Virtual Office page. This initiates the process of importing the firewall's self-signed certificate onto the web browser. This option only applies to the Internet Explorer browser on PCs running Windows 2000 or Windows XP.
• Enable HTTP meta tags for cache control - Inserts HTTP tags into the browser that instruct the web browser not to cache the Virtual Office page. SonicWALL recommends enabling this option.
The Customized Logo field displays a logo other than the Dell SonicWALL logo at the top of the Virtual Office portal. Enter the URL of the logo in the Customized Logo field. The logo must be in GIF format of size 155 x 36, and a transparent or light background is recommended.
SSL VPN > Client Settings
The SSL VPN > Client Settings page allows the administrator to enable SSL VPN access on zones and configure the client address range information and NetExtender client settings. It also displays which zones have SSL VPN access enabled.
The following tasks are configured on the SSL VPN > Client Settings page:
• Configuring Zones for SSL VPN Access
• Configuring the SSL VPN Client Address Range
• Configuring NetExtender Client Settings
Configuring Zones for SSL VPN Access
All of the zones on the firewall are displayed in the SSL VPN Status on Zones section of the SSL VPN > Client Settings page. SSL VPN access must be enabled on a zone before users can access the Virtual Office web portal. A green button to the left of the name of the zone indicates that SSL VPN access is enabled. A red button indicates that SSL VPN access is disabled. To change the SSL VPN access for a zone, simply click the name of the zone on the SSL VPN > Client Settings page.
SSL VPN Access can also be configured on the Network > Zones page by clicking the configure icon for the zone.
Note For SonicOS to terminate SSL VPN sessions, HTTPS for Management or User Login must be enabled on the Network > Interfaces page, in the Edit Interface dialog for the WAN interface.
Configuring the SSL VPN Client Address Range
The SSL VPN Client Address Range defines the IP address pool from which addresses will be assigned to remote users during NetExtender sessions. The range needs to be large enough to accommodate the maximum number of concurrent NetExtender users you wish to support plus one (for example, the range for 15 users requires 16 addresses, such as 192.168.200.100 to 192.168.200.115).
Note The range must fall within the same subnet as the interface to which the SSL VPN appliance is connected, and in cases where there are other hosts on the same segment as the SSL VPN appliance, it must not overlap or collide with any assigned addresses.
To configure the SSL VPN Client Address Range, perform the following steps:
1. Navigate to the SSL VPN > Client Settings page.
SSLVPN Client Address Range
2. In the NetExtender Start IP field, enter the first IP address in the client address range.
3. In the NetExtender End IP field, enter the last IP address in the client address range.
4. In the DNS Server 1 field, enter the IP address of the primary DNS server, or click the Default DNS Settings to use the default settings.
5. (Optional) In the DNS Server 2 field, enter the IP address of the backup DNS server.
6. (Optional) In the DNS Domain field, enter the domain name for the DNS servers.
7. In the User Domain field, enter the domain name for the users. The value of this field must match the domain field in the NetExtender client.
8. (Optional) In the WINS Server 1 field, enter the IP address of the primary WINS server.
9. (Optional) In the WINS Server 2 field, enter the IP address of the backup WINS server.
10. In the Interface pull-down menu, select the interface to be used for SSL VPN services.
Note The IP address range must be on the same subnet as the interface used for SSL VPN services.
11. Click the Zone name at the top of the page to enable SSL VPN access on it with these settings. The indicator should be green for the Zone you want to enable.
12. Click Accept.
Configuring NetExtender Client Settings
NetExtender client settings are configured on the bottom of the SSL VPN > Client Settings page. The following settings to customize the behavior of NetExtender when users connect and disconnect.
• Default Session Timeout (minutes) - The default timeout value for client inactivity, after which the client's session is terminated.
• Enable Web Management over SSLVPN - Enables or disables the NetExtender client to be managed over an SSLVPN connection using a Web browser.
• Enable SSH Management over SSLVPN - Enables or disables the NetExtender client to be managed over an SSLVPN connection using a Secure Shell (SSH) application.
• Enable NetBIOS Over SSLVPN - Allows NetExtender clients to broadcast NetBIOS to the SSL VPN subnet.
• Enable Client Autoupdate - The NetExtender client checks for updates every time it is launched.
• Exit Client After Disconnect - The NetExtender client exits when it becomes disconnected from the SSL VPN server. To reconnect, users will have to either return to the SSL VPN portal or launch NetExtender from their Programs menu.
• Uninstall Client After Exit - The NetExtender client automatically uninstalls when it becomes disconnected from the SSL VPN server. To reconnect, users will have to return to the SSL VPN portal. Capdvhs firewire drivers.
• Create Client Connection Profile - The NetExtender client will create a connection profile recording the SSL VPN Server name, the Domain name and optionally the username and password.
• Communication Between Clients - Enables NetExtender clients that are connected to the same server to communicate.
• User Name & Password Caching - Provide flexibility in allowing users to cache their usernames and passwords in the NetExtender client. The three options are Allow saving of user name only, Allow saving of user name & password, and Prohibit saving of user name & password. These options enable administrators to balance security needs against ease of use for users.
SSL VPN > Client Routes
The SSL VPN > Client Routes page allows the administrator to control the network access allowed for SSL VPN users. The NetExtender client routes are passed to all NetExtender clients and are used to govern which private networks and resources remote user can access via the SSL VPN connection.
The following tasks are configured on the SSL VPN > Client Routes page:
• Configuring Tunnel All Mode
• Adding Client Routes
Configuring Tunnel All Mode
Select Enabled from the Tunnel All Mode drop-down list to force all traffic for NetExtender users over the SSL VPN NetExtender tunnel—including traffic destined for the remote user's local network. This is accomplished by adding the following routes to the remote client's route table:
|
NetExtender also adds routes for the local networks of all connected Network Connections. These routes are configured with higher metrics than any existing routes to force traffic destined for the local network over the SSL VPN tunnel instead. For example, if a remote user is has the IP address 10.0.67.64 on the 10.0.*.* network, the route 10.0.0.0/255.255.0.0 is added to route traffic through the SSL VPN tunnel.
Note To configure Tunnel All Mode, you must also configure an address object for 0.0.0.0, and assign SSL VPN NetExtender users and groups to have access to this address object.
To configure SSL VPN NetExtender users and groups for Tunnel All Mode, perform the following steps. Aud file converter.
1. Navigate to the Users > Local Users or Users > Local Groups page.
2. Click on the Configure button for an SSL VPN NetExtender user or group.
3. Click on the VPN Access tab.
The following tasks are configured on the SSL VPN > Client Settings page:
• Configuring Zones for SSL VPN Access
• Configuring the SSL VPN Client Address Range
• Configuring NetExtender Client Settings
Configuring Zones for SSL VPN Access
All of the zones on the firewall are displayed in the SSL VPN Status on Zones section of the SSL VPN > Client Settings page. SSL VPN access must be enabled on a zone before users can access the Virtual Office web portal. A green button to the left of the name of the zone indicates that SSL VPN access is enabled. A red button indicates that SSL VPN access is disabled. To change the SSL VPN access for a zone, simply click the name of the zone on the SSL VPN > Client Settings page.
SSL VPN Access can also be configured on the Network > Zones page by clicking the configure icon for the zone.
Note For SonicOS to terminate SSL VPN sessions, HTTPS for Management or User Login must be enabled on the Network > Interfaces page, in the Edit Interface dialog for the WAN interface.
Configuring the SSL VPN Client Address Range
The SSL VPN Client Address Range defines the IP address pool from which addresses will be assigned to remote users during NetExtender sessions. The range needs to be large enough to accommodate the maximum number of concurrent NetExtender users you wish to support plus one (for example, the range for 15 users requires 16 addresses, such as 192.168.200.100 to 192.168.200.115).
Note The range must fall within the same subnet as the interface to which the SSL VPN appliance is connected, and in cases where there are other hosts on the same segment as the SSL VPN appliance, it must not overlap or collide with any assigned addresses.
To configure the SSL VPN Client Address Range, perform the following steps:
1. Navigate to the SSL VPN > Client Settings page.
SSLVPN Client Address Range
2. In the NetExtender Start IP field, enter the first IP address in the client address range.
3. In the NetExtender End IP field, enter the last IP address in the client address range.
4. In the DNS Server 1 field, enter the IP address of the primary DNS server, or click the Default DNS Settings to use the default settings.
5. (Optional) In the DNS Server 2 field, enter the IP address of the backup DNS server.
6. (Optional) In the DNS Domain field, enter the domain name for the DNS servers.
7. In the User Domain field, enter the domain name for the users. The value of this field must match the domain field in the NetExtender client.
8. (Optional) In the WINS Server 1 field, enter the IP address of the primary WINS server.
9. (Optional) In the WINS Server 2 field, enter the IP address of the backup WINS server.
10. In the Interface pull-down menu, select the interface to be used for SSL VPN services.
Note The IP address range must be on the same subnet as the interface used for SSL VPN services.
11. Click the Zone name at the top of the page to enable SSL VPN access on it with these settings. The indicator should be green for the Zone you want to enable.
12. Click Accept.
Configuring NetExtender Client Settings
NetExtender client settings are configured on the bottom of the SSL VPN > Client Settings page. The following settings to customize the behavior of NetExtender when users connect and disconnect.
• Default Session Timeout (minutes) - The default timeout value for client inactivity, after which the client's session is terminated.
• Enable Web Management over SSLVPN - Enables or disables the NetExtender client to be managed over an SSLVPN connection using a Web browser.
• Enable SSH Management over SSLVPN - Enables or disables the NetExtender client to be managed over an SSLVPN connection using a Secure Shell (SSH) application.
• Enable NetBIOS Over SSLVPN - Allows NetExtender clients to broadcast NetBIOS to the SSL VPN subnet.
• Enable Client Autoupdate - The NetExtender client checks for updates every time it is launched.
• Exit Client After Disconnect - The NetExtender client exits when it becomes disconnected from the SSL VPN server. To reconnect, users will have to either return to the SSL VPN portal or launch NetExtender from their Programs menu.
• Uninstall Client After Exit - The NetExtender client automatically uninstalls when it becomes disconnected from the SSL VPN server. To reconnect, users will have to return to the SSL VPN portal. Capdvhs firewire drivers.
• Create Client Connection Profile - The NetExtender client will create a connection profile recording the SSL VPN Server name, the Domain name and optionally the username and password.
• Communication Between Clients - Enables NetExtender clients that are connected to the same server to communicate.
• User Name & Password Caching - Provide flexibility in allowing users to cache their usernames and passwords in the NetExtender client. The three options are Allow saving of user name only, Allow saving of user name & password, and Prohibit saving of user name & password. These options enable administrators to balance security needs against ease of use for users.
SSL VPN > Client Routes
The SSL VPN > Client Routes page allows the administrator to control the network access allowed for SSL VPN users. The NetExtender client routes are passed to all NetExtender clients and are used to govern which private networks and resources remote user can access via the SSL VPN connection.
The following tasks are configured on the SSL VPN > Client Routes page:
• Configuring Tunnel All Mode
• Adding Client Routes
Configuring Tunnel All Mode
Select Enabled from the Tunnel All Mode drop-down list to force all traffic for NetExtender users over the SSL VPN NetExtender tunnel—including traffic destined for the remote user's local network. This is accomplished by adding the following routes to the remote client's route table:
|
NetExtender also adds routes for the local networks of all connected Network Connections. These routes are configured with higher metrics than any existing routes to force traffic destined for the local network over the SSL VPN tunnel instead. For example, if a remote user is has the IP address 10.0.67.64 on the 10.0.*.* network, the route 10.0.0.0/255.255.0.0 is added to route traffic through the SSL VPN tunnel.
Note To configure Tunnel All Mode, you must also configure an address object for 0.0.0.0, and assign SSL VPN NetExtender users and groups to have access to this address object.
To configure SSL VPN NetExtender users and groups for Tunnel All Mode, perform the following steps. Aud file converter.
1. Navigate to the Users > Local Users or Users > Local Groups page.
2. Click on the Configure button for an SSL VPN NetExtender user or group.
3. Click on the VPN Access tab.
4. Select the WAN RemoteAccess Networks address object and click the right arrow (->) button.
5. Click OK.
6. Repeat steps 1 through 5 for all local users and groups that use SSL VPN NetExtender.
Adding Client Routes
The Add Client Routes pull-down menu is used to configure access to network resources for SSL VPN users. Select the address object to which you want to allow SSL VPN access. Select Create new address object to create a new address object. Creating client routes causes access rules to automatically be created to allow this access. Alternatively, you can manually configure access rules for the SSL VPN zone on the Firewall > Access Rules page. For more information, see Firewall > Access Rules.
Netextender Download
Note After configuring Client Routes for SSL VPN, you must also configure all SSL VPN NetExtender users and user groups to be able to access the Client Routes on the Users > Local Users or Users > Local Groups pages.
To configure SSL VPN NetExtender users and groups to access Client Routes, perform the following steps.
1. Navigate to the Users > Local Users or Users > Local Groups page.
2. Click on the Configure button for an SSL VPN NetExtender user or group.
3. Click on the VPN Access tab.
4. Select the address object for the Client Route, and click the right arrow (->) button.
5. Click OK.
6. Repeat steps 1 through 5 for all local users and groups that use SSL VPN NetExtender.
SSL_VPN
SSL VPN
This chapter provides information on how to configure the SSL VPN features on the SonicWALL security appliance. SonicWALL's SSL VPN features provide secure remote access to the network using the NetExtender client.
NetExtender is an SSL VPN client for Windows, Mac, or Linux users that is downloaded transparently and that allows you to run any application securely on the company's network. It uses Point-to-Point Protocol (PPP). NetExtender allows remote clients seamless access to resources on your local network. Users can access NetExtender two ways:
Logging in to the Virtual Office web portal provided by the SonicWALL security appliance and clicking on the NetExtender button.
Launching the standalone NetExtender client.
The NetExtender standalone client is installed the first time you launch NetExtender. Thereafter, it can be accessed directly from the Start menu on Windows systems, from the Application folder or dock on MacOS systems, or by the path name or from the shortcut bar on Linux systems.
This chapter contains the following sections:
SSL VPN NetExtender Overview
This section provides an introduction to the SonicOS Enhanced SSL VPN NetExtender feature. This section contains the following subsections:
What is SSL VPN NetExtender?
SonicWALL's SSL VPN NetExtender feature is a transparent software application for Windows, Mac, and Linux users that enables remote users to securely connect to the remote network. With NetExtender, remote users can securely run any application on the remote network. Users can upload and download files, mount network drives, and access resources as if they were on the local network. The NetExtender connection uses a Point-to-Point Protocol (PPP) connection.
Benefits
NetExtender provides remote users with full access to your protected internal network. The experience is virtually identical to that of using a traditional IPSec VPN client, but NetExtender does not require any manual client installation. Instead, the NetExtender Windows client is automatically installed on a remote user's PC by an ActiveX control when using the Internet Explorer browser, or with the XPCOM plugin when using Firefox. On MacOS systems, supported browsers use Java controls to automatically install NetExtender from the Virtual Office portal. Linux systems can also install and use the NetExtender client.
After installation, NetExtender automatically launches and connects a virtual adapter for secure SSL-VPN point-to-point access to permitted hosts and subnets on the internal network.
NetExtender Concepts
Sonicwall Netextender For Mac Remote Desktop
The following sections describe advanced NetExtender concepts:
Stand-Alone Client
NetExtender is a browser-installed lightweight application that provides comprehensive remote access without requiring users to manually download and install the application. The first time a user launches NetExtender, the NetExtender stand-alone client is automatically installed on the user's PC or Mac. The installer creates a profile based on the user's login information. The installer window then closes and automatically launches NetExtender. If the user has a legacy version of NetExtender installed, the installer will first uninstall the old NetExtender and install the new version.
Once the NetExtender stand-alone client has been installed, Windows users can launch NetExtender from their PC's Start > Programs menu and configure NetExtender to launch when Windows boots. Mac users can launch NetExtender from their system Applications folder, or drag the icon to the dock for quick access. On Linux systems, the installer creates a desktop shortcut in /usr/share/NetExtender. This can be dragged to the shortcut bar in environments like Gnome and KDE.
Client Routes
NetExtender client routes are used to allow and deny access for SSL VPN users to various network resources. Address objects are used to easily and dynamically configure access to network resources.
Tunnel All Mode
Tunnel All mode routes all traffic to and from the remote user over the SSL VPN NetExtender tunnel—including traffic destined for the remote user's local network. This is accomplished by adding the following routes to the remote client's route table:
|
NetExtender also adds routes for the local networks of all connected Network Connections. These routes are configured with higher metrics than any existing routes to force traffic destined for the local network over the SSL VPN tunnel instead. For example, if a remote user is has the IP address 10.0.67.64 on the 10.0.*.* network, the route 10.0.0.0/255.255.0.0 is added to route traffic through the SSL VPN tunnel.
Tunnel All mode is configured on the SSL VPN > Client Routes page.
Connection Scripts
SonicWALL SSL VPN provides users with the ability to run batch file scripts when NetExtender connects and disconnects. The scripts can be used to map or disconnect network drives and printers, launch applications, or open files or Web sites. NetExtender Connection Scripts can support any valid batch file commands.
Proxy Configuration
SonicWALL SSL VPN supports NetExtender sessions using proxy configurations. Currently, only HTTPS proxy is supported. When launching NetExtender from the Web portal, if your browser is already configured for proxy access, NetExtender automatically inherits the proxy settings. The proxy settings can also be manually configured in the NetExtender client preferences. NetExtender can automatically detect proxy settings for proxy servers that support the Web Proxy Auto Discovery (WPAD) Protocol.
NetExtender provides three options for configuring proxy settings:
Automatically detect settings - To use this setting, the proxy server must support Web Proxy Auto Discovery Protocol (WPAD)), which can push the proxy settings script to the client automatically.
Use automatic configuration script - If you know the location of the proxy settings script, you can select this option and provide the URL of the script.
Use proxy server - You can use this option to specify the IP address and port of the proxy server. Optionally, you can enter an IP address or domain in the BypassProxy field to allow direct connections to those addresses and bypass the proxy server. If required, you can enter a user name and password for the proxy server. If the proxy server requires a username and password, but you do not specify them, a NetExtender pop-up window will prompt you to enter them when you first connect.
When NetExtender connects using proxy settings, it establishes an HTTPS connection to the proxy server instead of connecting to the SonicWALL security appliance. server directly. The proxy server then forwards traffic to the SSL VPN server. All traffic is encrypted by SSL with the certificate negotiated by NetExtender, of which the proxy server has no knowledge. The connecting process is identical for proxy and non-proxy users.
Configuring Users for SSL VPN Access
In order for users to be able to access SSL VPN services, they must be assigned to the SSLVPN Services group. Users who attempt to login through the Virtual Office who do not belong to the SSLVPN Services group will be denied access. The following sections describe how to configure user accounts for SSL VPN access:
Configuring SSL VPN Access for Local Users
To configure users in the local user database for SSL VPN access, you must add the users to the SSLVPN Services user group. To do so, perform the following steps:
Navigate to the Users > Local Users page.
Click on the configure icon for the user you want to edit, or click the Add User button to create a new user. The Edit User window is launched.
Click on the Groups tab.
In the User Groups column, click on SSLVPN Services and click the right arrow to move it to the Member Of column.
Click on the VPN Access tab. The VPN Access tab configures which network resources VPN users (either GVC, NetExtender, or Virtual Office bookmarks) can access. Select one or more network address objects or groups from the Networks list and click the right arrow button (->) to move them to the Access List column. To remove the user's access to a network address objects or groups, select the network from the Access List, and click the left arrow button (<-).
Click OK.
NoteThe VPN access tab affects the ability of remote clients using GVC, NetExtender, and SSL VPN Virtual Office bookmarks to access network resources. To allow GVC, NetExtender, or Virtual Office users to access a network resource, the network address objects or groups must be added to the 'allow' list on the VPN Access tab.
NoteThe feature, One-Time Password, is a two-factor authentication scheme utilizing system-generated, random passwords, in addition to standard user name and password credentials, for users attempting to login through SSL VPN connections. For more information on configuring this feature, see 'One-Time Password' section on page 807.
Configuring SSL VPN Access for RADIUS Users
To configure RADIUS users for SSL VPN access, you must add the users to the SSLVPN Services user group. To do so, perform the following steps:
Navigate to the Users > Settings page.
In the Authentication Method for login pulldown menu, select RADIUS or RADIUS + Local Users.
Click the Configure button for Authentication Method for login. The RADIUS Configuration window displays.
Click on the RADIUS Users tab.
In the Default user group to which all RADIUS users belong pulldown menu, select SSLVPN Services.
Click OK.
NoteThe VPN Access tab in the Edit User window is also another granular control on access for both Virtual Office Bookmarks and for NetExtender access.
Configuring SSL VPN Access for LDAP Users
To configure LDAP users for SSL VPN access, you must add the LDAP user groups to the SSLVPN Services user group. To do so, perform the following steps:
Navigate to the Users > Settings page.
Set the Authentication method for login to either LDAP or LDAP + Local Users.
Click the Configure button to launch the LDAP Configuration window.
Click on the LDAP Users tab.
In the Default LDAP User Group pulldown menu, select SSLVPN Services.
Click OK.
NoteThe VPN Access tab n the Edit User window is also another granular control on access for both Virtual Office Bookmarks and for NetExtender access.
SSL VPN > Status
The SSL VPN > Status page displays a summary of active NetExtender sessions, including the name, the PPP IP address, the physical IP address, login time, length of time logged in and logout time.
The following table provides a description of the status items.
|
SSL VPN > Server Settings
The SSL VPN > Server Settings page is used to configure details of the SonicWALL security appliance's behavior as an SSL VPN server.
The following options can be configured on the SSL VPN > Server Settings page.
SSL VPN Status on Zones: This displays the SSL VPN Access status on each Zone. Green indicates active SSL VPN status, while red indicates inactive SSL VPN status. To enable or disable SSL-VPN access on a zone, click on the zone name to jump to the Edit Zone window.
SSL VPN Port: Set the SSL VPN port for the appliance. The default is 4433.
Certificate Selection: Select the certificate that will be used to authenticate SSL VPN users. To manage certificates, go to the Network > Certificates page.
Enable Server Cipher Preference: Select this checkbox to configure a prefered cipher method. The available ciphers are RC4_MD5, 3DES_SHA1, and AES256_SHA1.
RADIUS User Settings: This option is only available when either RADIUS or LDAP is configured to authenticate SSL VPN users. Select the Use RADIUS in checkbox to have RADIUS use MSCHAP (or MSCHAPv2) mode. Enabling MSCHAP-mode RADIUS will allow users to change expired passwords at login time.
NoteIn LDAP, password updates can only be done when using either Novell eDirectory or Active Directory with TLS and binding to it using an administrative account. If LDAP is not configured as such, password updates for SSL VPN users will be performed using MSCHAP-mode RADIUS, after using LDAP to authenticate the user.
SSL VPN > Client Settings
NoteThe SSL VPN > Client Settings page is moved to the SSL VPN > Remote Access EPC page. Client settings are now configured for each EPC profile.
Sonicwall Netextender For Mac
If Remote Access EPC is not licensed or supported on your box, please click the Configure icon for the 'Default Device Profile for Windows' to configure client settings for NetExtender users.
For more information, see SSL VPN > Remote Access EPC.
SSL VPN > Portal Settings
The SSL VPN > Portal Settings page is used to configure the appearance and functionality of the SSL VPN Virtual Office web portal. The Virtual Office portal is the website that uses log in to launch NetExtender. It can be customized to match any existing company website or design style.
The following settings configure the appearance of the Virtual Office portal:
Portal Site Title - The text displayed in the top title of the web browser.
Portal Banner Title - The the text displayed next to the logo at the top of the page.
Home Page Message - The HTML code that is displayed above the NetExtender icon.
Login Message - The HTML code that is displayed when users are prompted to log in to the Virtual Office.
Example Template - Resets the Home Page Message and Login Message fields to the default example template.
Preview - Launch a pop-up window that displays the HTML code.
The following options customize the functionality of the Virtual Office portal:
Launch NetExtender after login - Automatically launches NetExtender after a user logs in.
Display Import Certificate Button - Displays an Import Certificate button on the Virtual Office page. This initiates the process of importing the SonicWALL security appliance's self-signed certificate onto the web browser. This option only applies to the Internet Explorer browser on PCs running Windows 2000 or Windows XP.
Enable HTTP meta tags for cache control - Inserts HTTP tags into the browser that instruct the web browser not to cache the Virtual Office page. SonicWALL recommends enabling this option.
Sonicwall Netextender For Mac Download
The Customized Logo field is used to display a logo other than the SonicWALL logo at the top of the Virtual Office portal. Enter the URL of the logo in the Customized Logo field. The logo must be in GIF format of size 155 x 36, and a transparent or light background is recommended.

